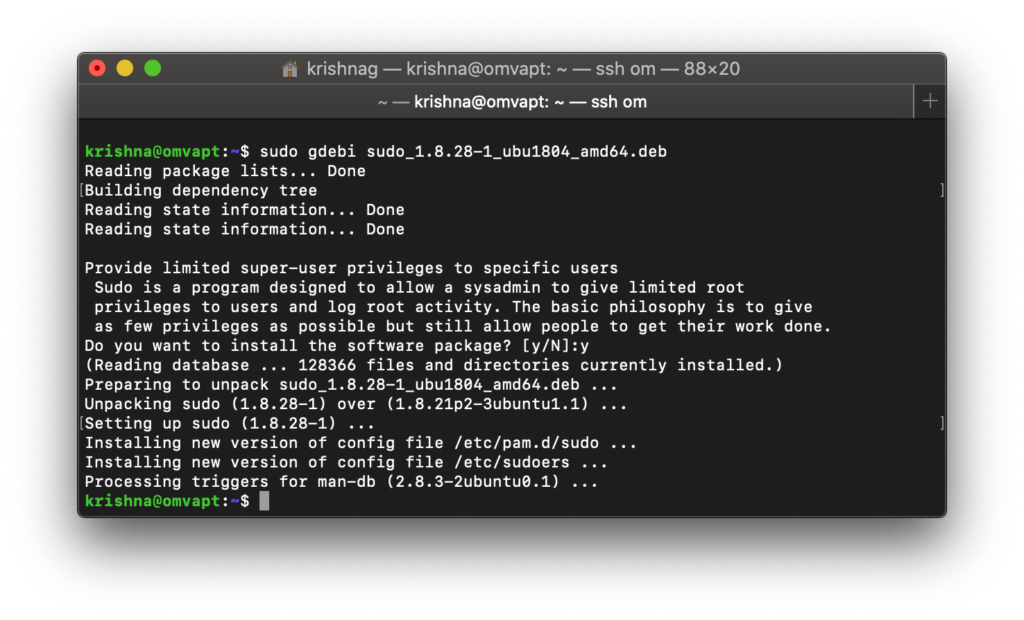
How to update sudo packages manually to fix the vulnerability Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted?
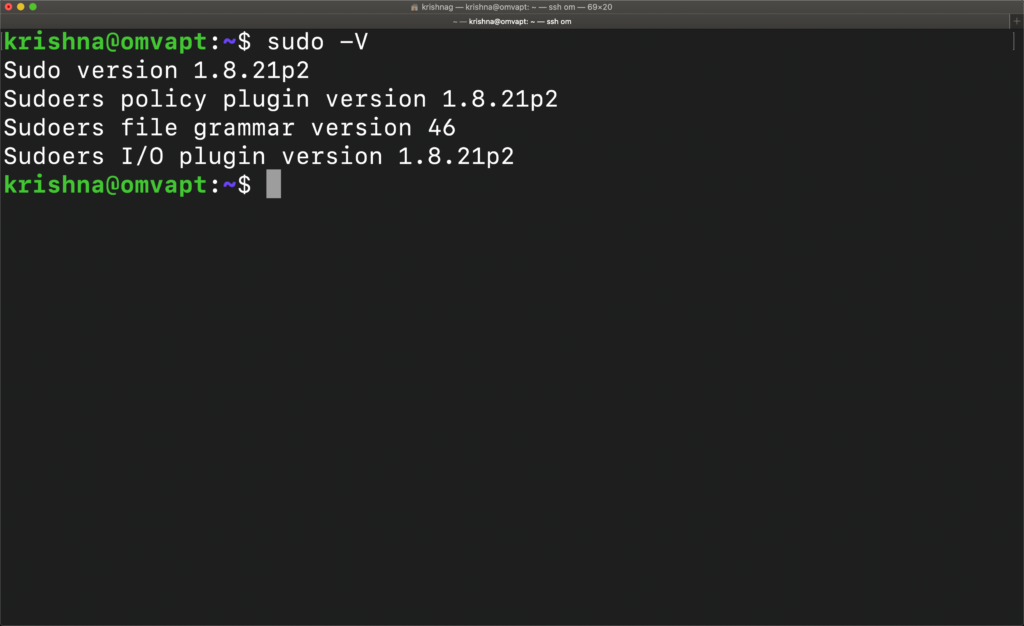
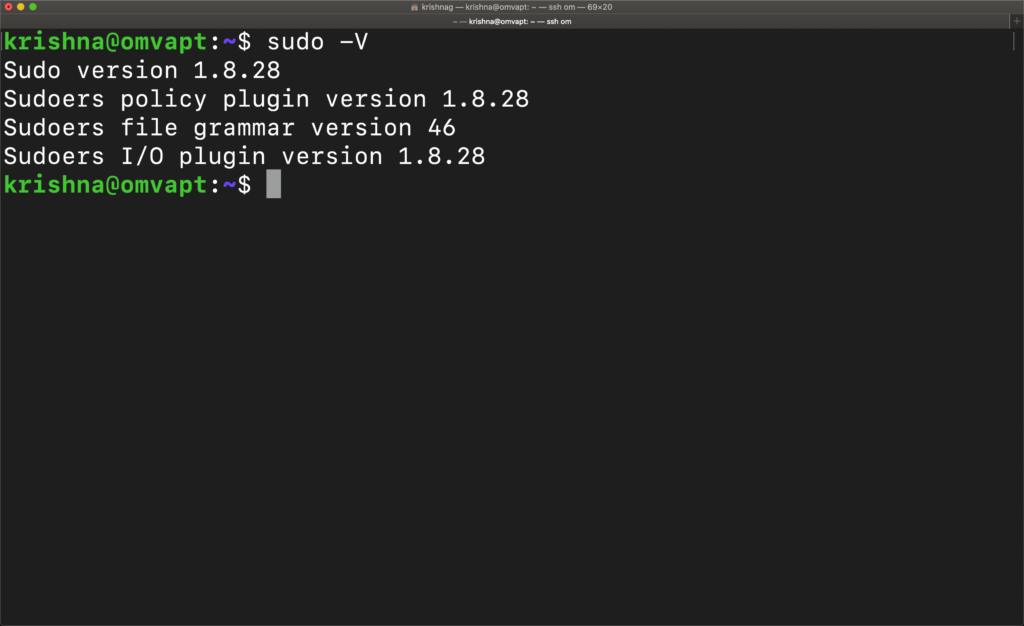
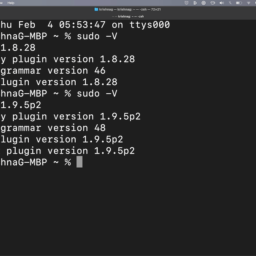
First, check the version by typing the command
sudo -V
Sudo version 1.8.21p2
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version
1.8.21p2
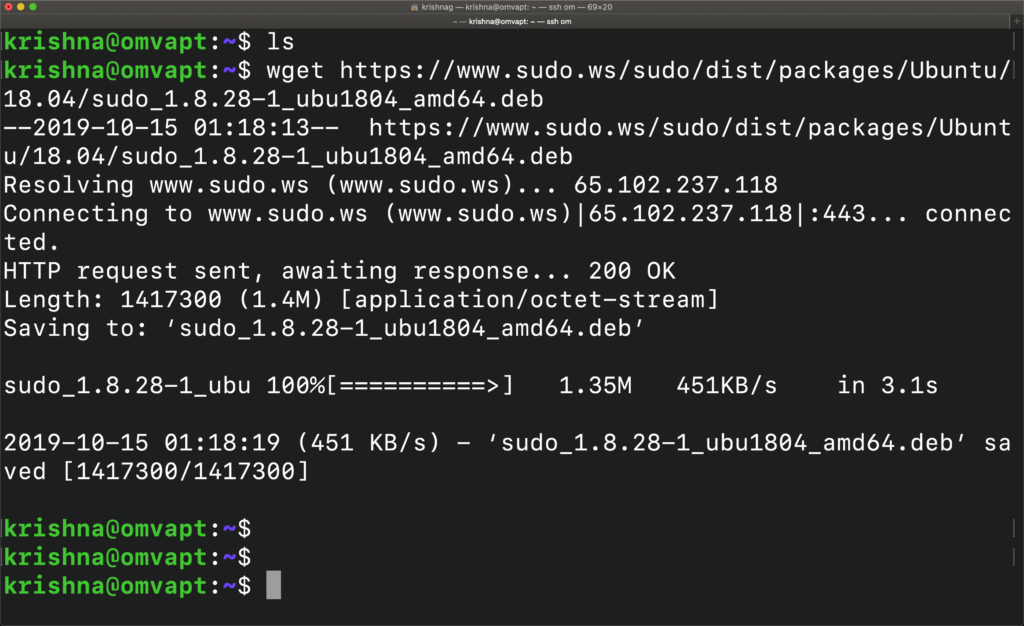
Let’s download the sudo packages from the repository manually. We can use either wget or curl -O
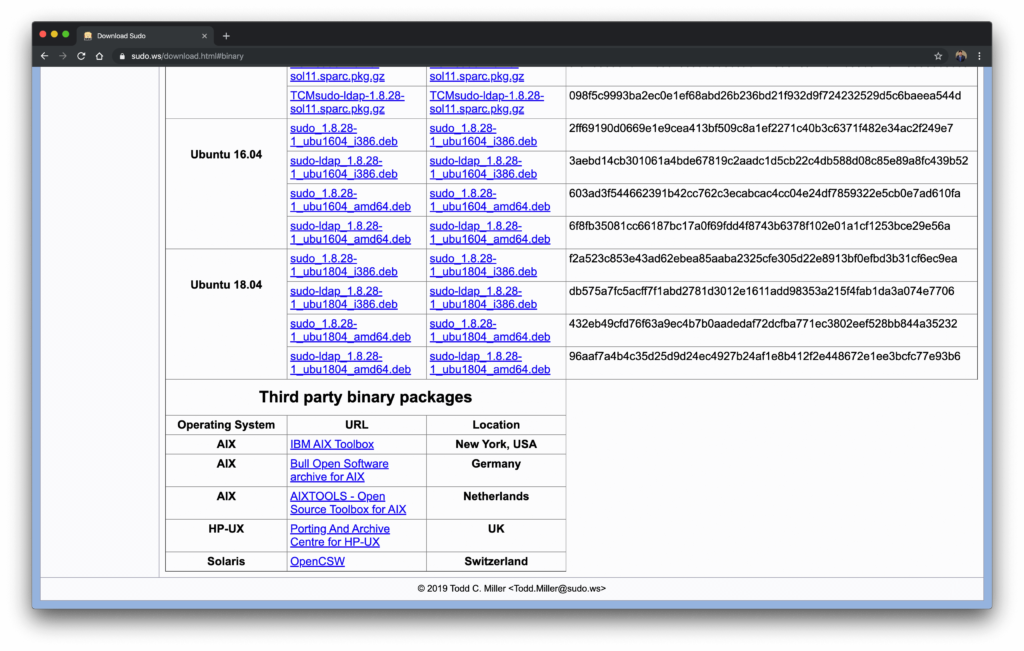
Copy the exact sudo package from the binary package list based upon the architecture.
https://www.sudo.ws/sudo/dist/packages/Ubuntu/18.04/sudo_1.8.28-1_ubu1804_amd64.deb
I have chosen 64-bit architecture as 32-bit architecture is not supported, anymore.
–2019-10-15 01:18:13– https://www.sudo.ws/sudo/dist/packages/Ubuntu/18.04/sudo_1.8.28-1_ubu1804_amd64.deb
Resolving www.sudo.ws (www.sudo.ws)… 65.102.237.118
Connecting to www.sudo.ws (www.sudo.ws)|65.102.237.118|:443… connected.
HTTP request sent, awaiting response… 200 OK
Length: 1417300 (1.4M) [application/octet-stream]
Saving to: ‘sudo_1.8.28-1_ubu1804_amd64.deb’
sudo_1.8.28-1_ubu 100%[==========>] 1.35M 451KB/s in 3.1s
2019-10-15 01:18:19 (451 KB/s) – ‘sudo_1.8.28-1_ubu1804_amd64.deb’ saved [1417300/14
17300]
Once it is downloaded, ensure it is present in the same directory for easy installation in the next following commands.
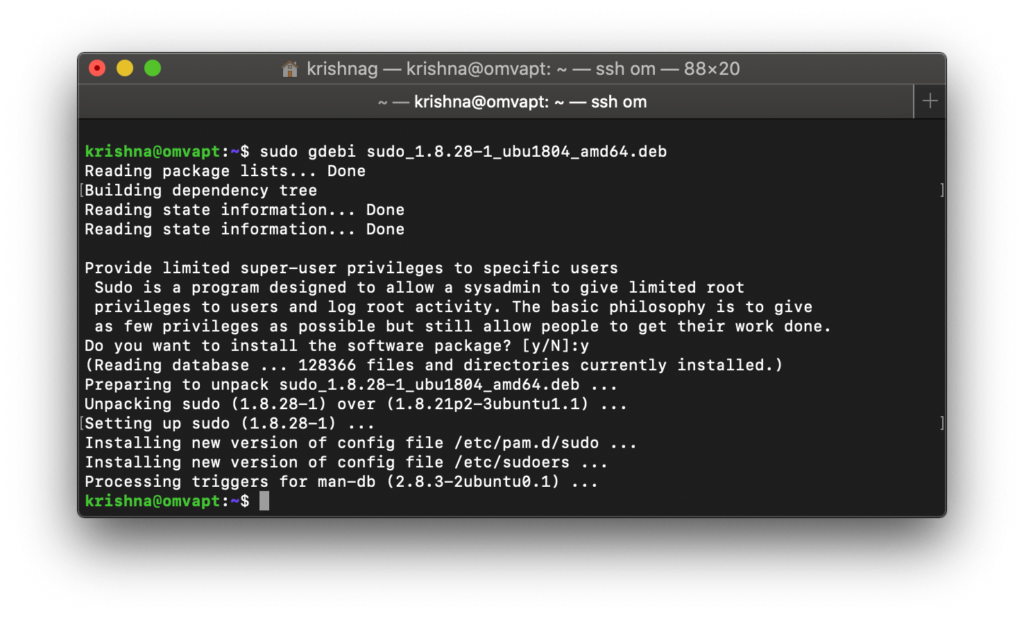
We also need to install gdebi to fetch the missing dependencies.
We are all set and now let’s upgrade the sudo package to remediate or fix the vulnerability of Linux privilege escalation for unauthorized users.
Finally, we have updated the sudo package from 1.8.21 to 1.8.28 by remediating the high severity vulnerability which is yet to be released/updated in the CVE database.
Although, CVE number has been assigned CVE-2019-14287. No information has been updated in the CVE details. As Ethical Hackers, we are not dependent entirely on CVE databases but also use our experience and skills to stay ahead of the curve.

Know more about the vulnerability in this link #Sudo #Flaw Lets #Linux Users #Run Commands As #Root Even When They’re #Restricted http://ow.ly/Q6Z650wLa6o