How to update sudo packages manually to fix the Buffer Overflow vulnerability CVE-2021-3156?
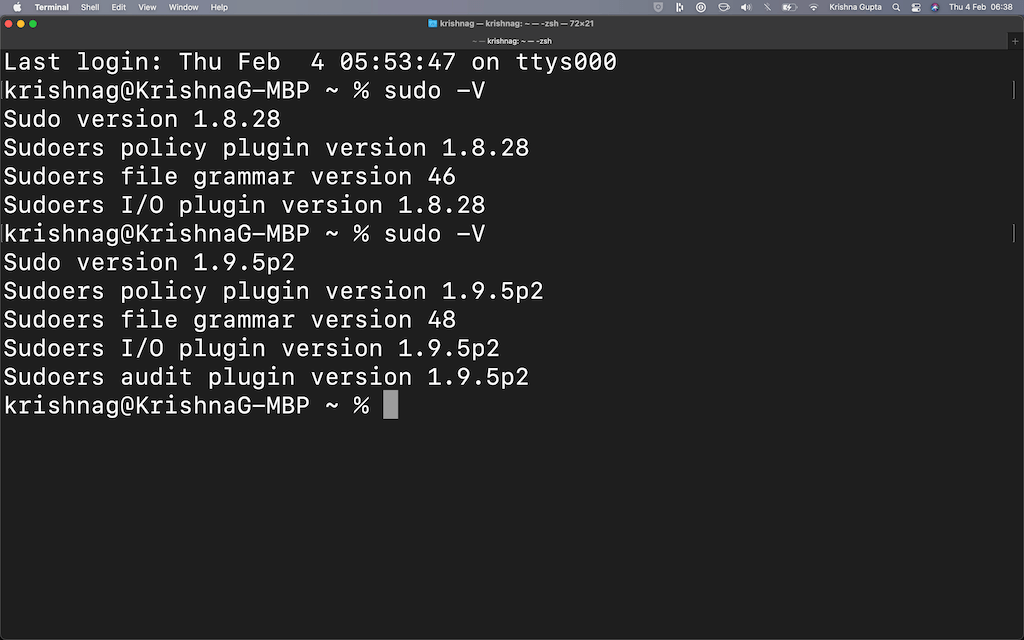
First, check the version by typing the command
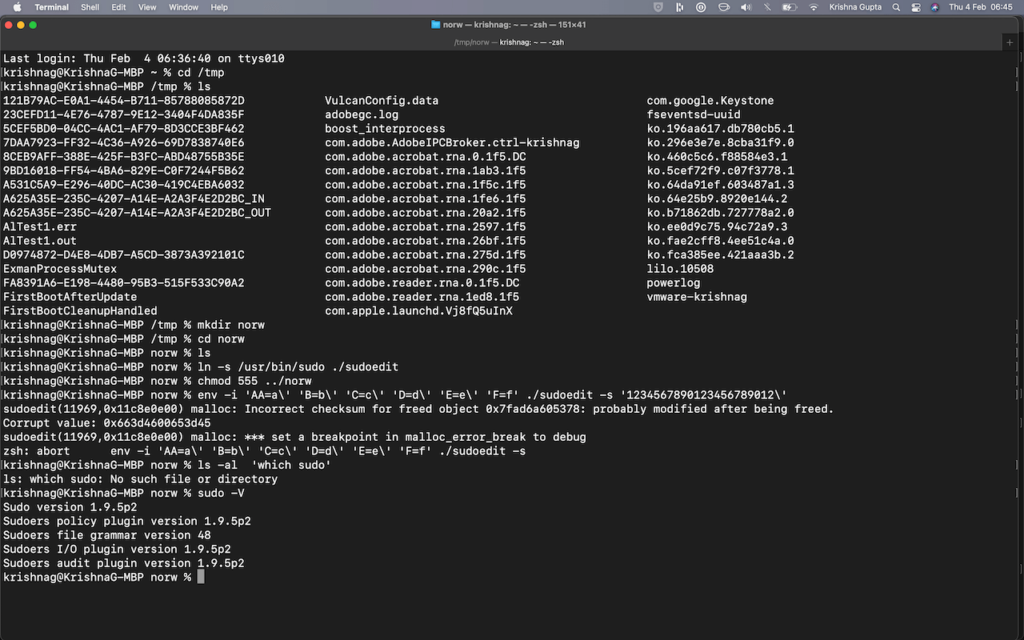
Krishnas-MBP:~ krishnagupta$ sudo -V
Sudo version 1.8.28
Sudoers policy plugin version 1.8.28
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.28
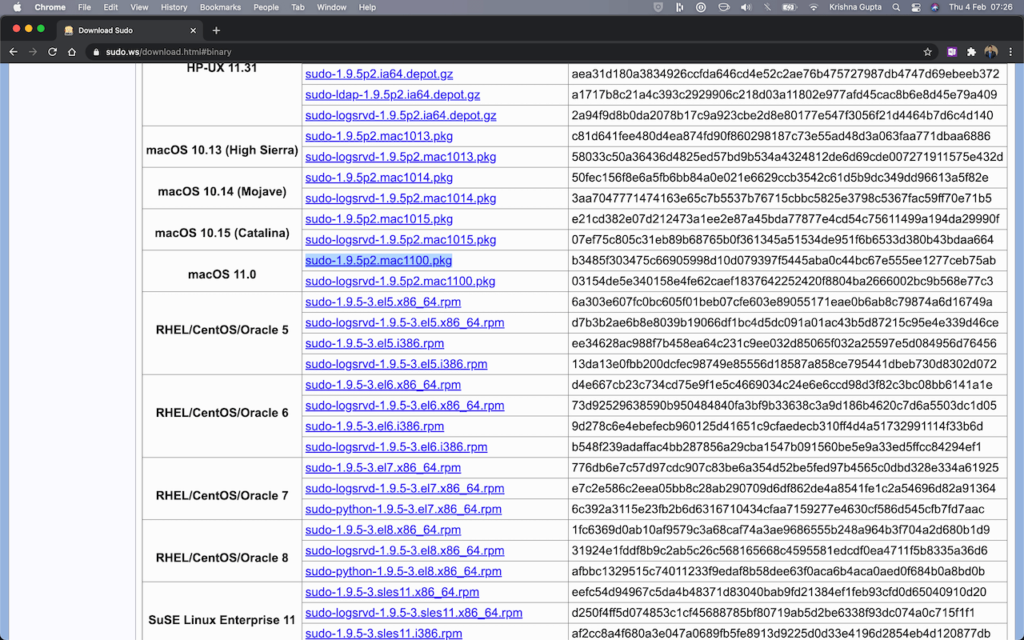
Second, Download the sudo updated version for macOS from the below link
https://github.com/sudo-project/sudo/releases/download/SUDO_1_9_5p2/sudo-1.9.5p2.mac1100.pkg
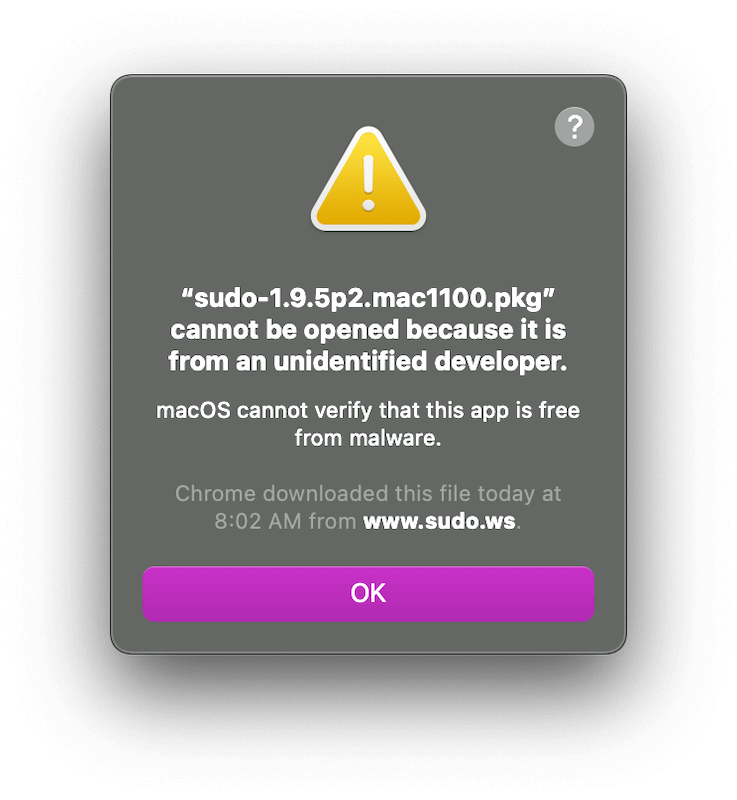
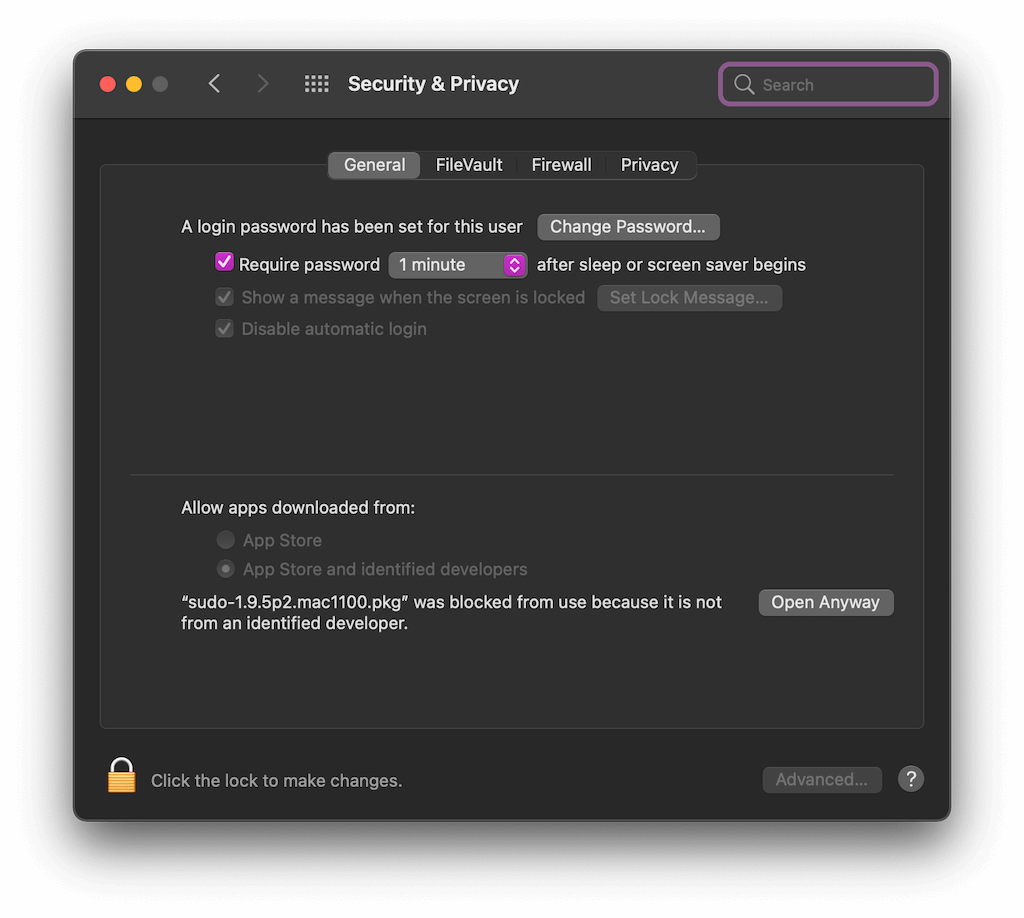
If it does not open then open the System Preferences > Security and Privacy > Click Open Anyway (note it should be sudo 1.9.5p2, the latest version as of 4Feb2021).
We are all set and now let’s upgrade the sudo package to remediate or fix the vulnerability of macOS privilege escalation for unauthorised users.
Finally, we have updated the sudo package from 1.8.31 to 1.9.5p2 by remediating the high severity vulnerability, which is yet to be released/updated in the CVE database.
The CVE number has been assigned CVE-2021-3156. As Ethical Hackers, we are not reliant entirely on CVE databases and use our experience and skills to stay ahead on the cutting edge skills.
To know more about the vulnerability and how it is exploited – https://vapt.me/macOSudo
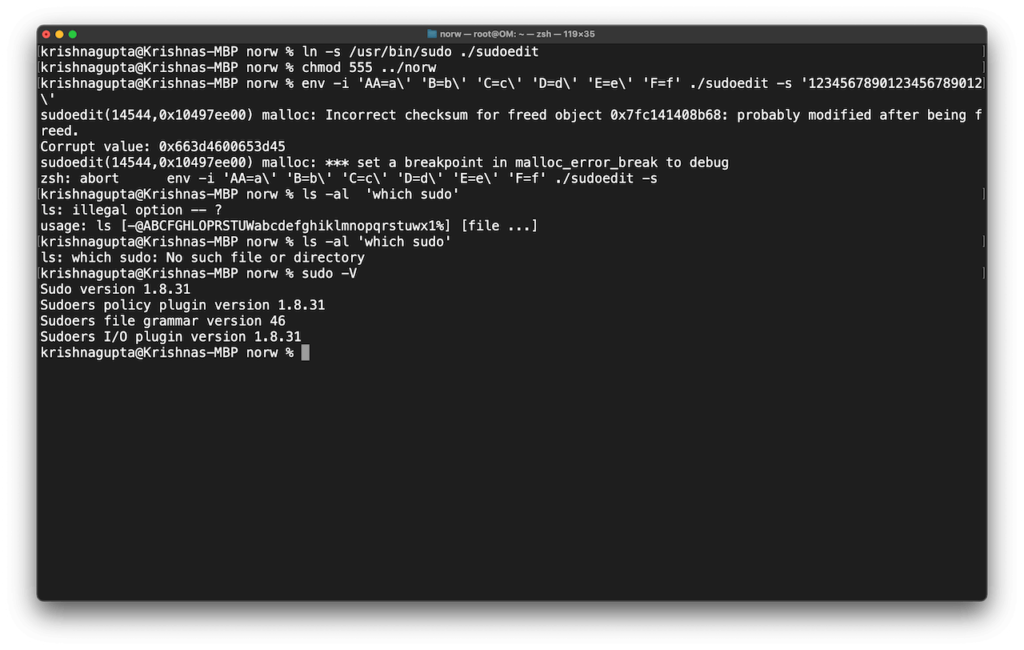
on macOS Big Sur 11.2 with sudo version 1.8.31
Although we could not exploit this vulnerability on macOS running 11.2 with sudo version 1.8.28 and 1.8.31. We have updated it to sudo version 1.9.5p2 as shown in the screenshot above.
Stay Safe and Happy Hacking if you are an ethical hacker.